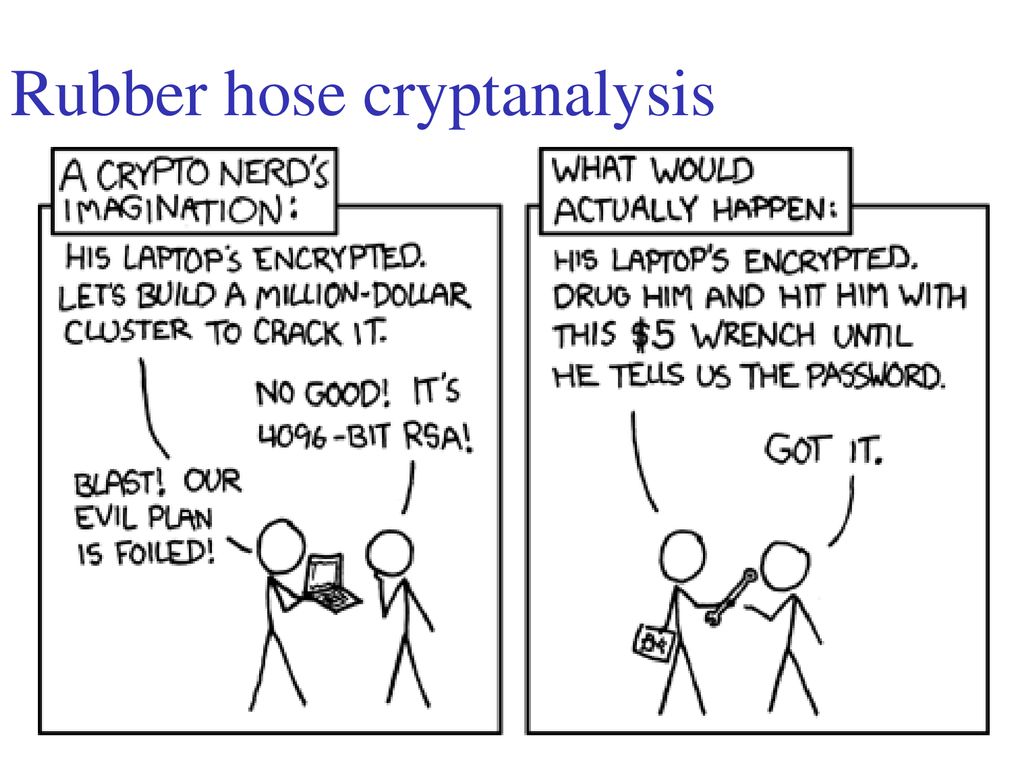
Anonymous Ghostwriters - Rubber Hose Cryptography works by filling the entire hard drive with random characters that are indistinguishable from encrypted data. The file system then takes each archive of real data

Amazon.co.jp: Rubber-Hose Cryptanalysis : Surhone, Lambert M., Timpledon, Miriam T., Marseken, Susan F.: Japanese Books

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks | USENIX

Neuroscience Meets Cryptography: Crypto Primitives Secure Against Rubber Hose Attacks | May 2014 | Communications of the ACM
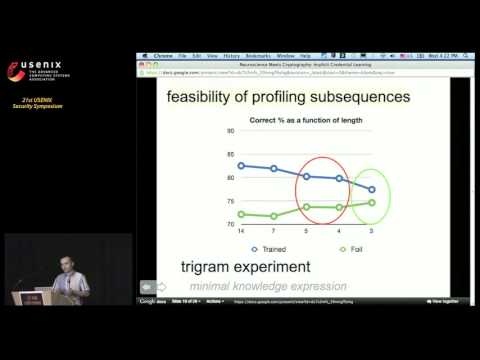
Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks - YouTube

Amazon.co.jp: Rubber-Hose Cryptanalysis : Surhone, Lambert M., Timpledon, Miriam T., Marseken, Susan F.: Japanese Books

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks A Paper by Hristo Bojinov, Daniel Sanchez, Paul Reber, - ppt download